by Aviv Raff on | Leave a comment
Filed under Research Lab and tagged Botnet, Cyber crime, DGA, Malware.
Filed under Research Lab and tagged Botnet, Cyber crime, DGA, Malware.
The advanced malware world is amazingly dynamic. Attackers adapt to the security vendors findings incredibly fast, so much so that sometimes they manage to make adaptations to the malware even before the malware report is public.
Yesterday, Dell SecureWorks and Damballa reported [PDF] that a variant of the PushDo malware added a new feature – a fallback mechanism for situations when the C&C server is not accessible. According to the report, in such cases, the malware will start using a Domain Generation Algorithm (DGA), which generates a list of 1380 .COM domains on a daily basis.
Now that the DGA is publicly known, it will be easier for on-premises security solutions to identify communication to the generated domains, hence allowing a better detection mechanism of PushDo infected machines.
The group behind PushDo probably figured out that they are being investigated by the security vendors, because it didn’t take them too long to adapt to this new reality and change their Domain Generation Algorithm. This new DGA now generates .KZ domains instead of .COM domains (See Figure 1). Not only that but there are now at least two new variants of PushDo that are being pushed to victims from several different hijacked websites.
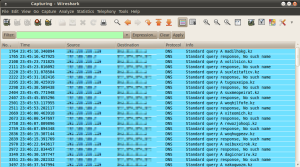 Figure 1: .kz domains generated by the new PushDo variant
Figure 1: .kz domains generated by the new PushDo variant
One of the hijacked websites is misconfigured and displays the list of files on the folder of PushDo variants. As you can see in the screenshot below, the PushDo gang uploaded the files, 5.exe and 6.exe, yesterday a few hours after noon Europe time, to this European hijacked web server.
Figure 2: Two new PushDo variants hosted on a hijacked website
We are still investigating these new variants of PushDo and we will update this blog post with new information when it becomes available.
The following are the MD5s of the new PushDo variants:
a3a2d02f754113ea8510f3a943a61414
21c44dc8ca3f1ded1bf245cee8048230

