Mahdi Numbers and the Flame "Connection"
In our previous blog post we discussed Mahdi, a malware campaign primarily targeting critical infrastructure companies, financial services and government embassies in Middle Eastern countries.
Through mutual research with Kaspersky Labs, we found that most of Mahdi’s targeted entities are from Iran and Israel. A report released by Symantec shortly after our public announcement however, suggested that over 72 percent of the victims are from Israel and that the Command-and-Control (C&C) servers are located in Azerbaijan.
72 percent of part of the attack
This 72 percent figure is somewhat true. Let us explain:
If you recall from our report, there are different Mahdi malware variants communicating with four different C&C servers. The first variants communicated with a domain ma[REMOVED]il.in which resolved back in December 2011 to an IP address in Tehran. A month later, variants resolved to 67.205.[REMOVED], which is a server located in Canada. Most of the variants communicating with this C&C server were indeed from Israel.
However, later that year, more variants were added to the attack campaign, communicating with three other C&C servers which are also located in Canada. Most of the targeted entities communicating with those three servers originate from Iran.
Symantec may have come up with 72 percent because they were only looking at variants which communicated with the C&C servers targeting entities from Israel. Or, maybe they are looking only at their customer’s machines which they found to be infected with Mahdi. As an American company Symantec is not allowed to sell their products to Iran and therefore they can’t see infections in Iran. At Seculert, we monitor global infections — no matter which country, without the need to install any software or hardware. This is why we were able to verify that most of the targeted entities are indeed from both Iran and Israel.
Not only the Middle East
Looking deeper into the Mahdi victims’ IP addresses, we did find a few dozen IP addresses which seem to be from non-middle eastern countries, such as the U.S and U.K. Although, those IP addresses were of targeted persons who seem to be visiting those countries, but were based in Middle Eastern countries.
The Flame “connection”
We originally decided to work with Kaspersky Labs in order to find similarities between Mahdi malware and Flame. While we did not find any direct connection between the campaigns, we did find one small and interesting link.
For each victim, the Mahdi malware assigns a unique identifier, which is used by the C&C server to identify which targeted entity it is communicating with. Part of this unique identifier is a prefix, which is used to help spread the targeted entities between the members of the attacking group and allow them to identify and manage a bulk of targeted entities. An example for a unique identifier is: abasMYCOMP123456, where “abas” is the prefix.
Targeted entities communicating with the 67.205.[REMOVED] C&C server are using the following prefixes:
- abaafghan
- abaanu
- abamo
- abas
- shelik
Targeted entities, communicating with the other three C&C servers are using the following prefixes:
- AJA
- Chabeharcoffinet
- Flame
- Iranshahrcoffinet
- Khashcoffinet
- Nikshahrcoffinet
- shelik
- selik
- Saravancoffinet
- Zabolcoffinet
You can see from the list above that one of the prefixes is “Flame”. The first targeted victim with the “Flame” prefix began communicating with the C&C server in early June, right after the Kaspersky Lab discovery of Flame went public. Coincidence? Maybe.
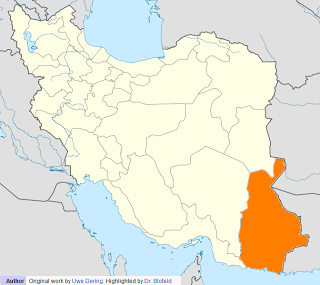
Another interesting thing to note is that some of the prefixes end with “coffinet”. These include: Chabehar, Iranshahr, Khash, Nikshahr, Saravan, Zabol, all of which are cities and counties located in the southeast region of Iran.
Am I part of the Mahdi Campaign?
In case you are wondering whether your device or network is compromised with the Mahdi malware, Seculert has set-up a free online tool. This tool allows anyone to easily find out if their IP address ever communicated with any of the four C&C servers participating in the Mahdi campaign. The free online tool is available here.
What’s next?
Our friends at Kaspersky Lab mentioned on their last blog post, that there is a new variant of Mahdi in the wild, which is communicating with a different C&C server. This C&C server is also located in Canada. Interestingly enough, the new Mahdi variant added the words “USA” and “gov” to its triggers list.
On our next blog post we will update you with information on the targeted entities which are communicating with this new C&C server.
You guys are an Israeli company so, just like Symantec, how could you guys have infection data from Iran?